Design and Analysis of Reversible Data Hiding Using Hybrid Cryptographic and Steganographic approaches for Multiple Images
Main Article Content
Abstract
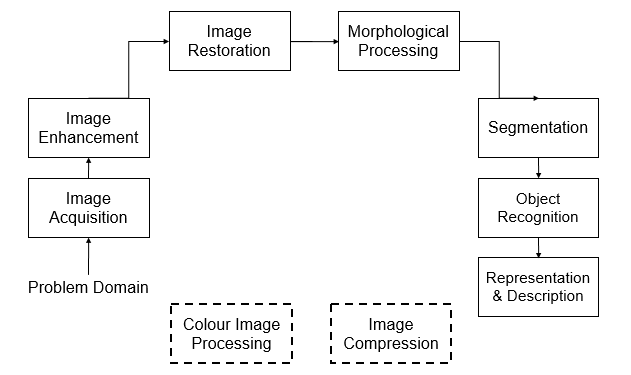
Data concealing is the process of including some helpful information on images. The majority of sensitive applications, such sending authentication data, benefit from data hiding. Reversible data hiding (RDH), also known as invertible or lossless data hiding in the field of signal processing, has been the subject of a lot of study. A piece of data that may be recovered from an image to disclose the original image is inserted into the image during the RDH process to generate a watermarked image. Lossless data hiding is being investigated as a strong and popular way to protect copyright in many sensitive applications, such as law enforcement, medical diagnostics, and remote sensing. Visible and invisible watermarking are the two types of watermarking algorithms. The watermark must be bold and clearly apparent in order to be visible. To be utilized for invisible watermarking, the watermark must be robust and visibly transparent. Reversible data hiding (RDH) creates a marked signal by encoding a piece of data into the host signal. Once the embedded data has been recovered, the original signal may be accurately retrieved. For photos shot in poor illumination, visual quality is more important than a high PSNR number. The DH method increases the contrast of the host picture while maintaining a high PSNR value. Histogram equalization may also be done concurrently by repeating the embedding process in order to relocate the top two bins in the input image's histogram for data embedding. It's critical to assess the images after data concealment to see how much the contrast has increased. Common picture quality assessments include peak signal to noise ratio (PSNR), relative structural similarity (RSS), relative mean brightness error (RMBE), relative entropy error (REE), relative contrast error (RCE), and global contrast factor (GCF). The main objective of this paper is to investigate the various quantitative metrics for evaluating contrast enhancement. The results show that the visual quality may be preserved by including a sufficient number of message bits in the input photographs.
Article Details

This work is licensed under a Creative Commons Attribution-NoDerivatives 4.0 International License.
References
Wen Zhang, Jie Men, Conglong Ma, “Research progress of applying digital watermarking technology for printing,” 2018.
David-Octavio Munoz-Ramirez, Volodymyr Ponomaryo, Rogelio Reyes-Reyes, Volodymyr Kyrychenko, OleksandrPechenin, Alexander Totsky ,“A Robust Watermarking Scheme to JPEG Compression for Embedding a Color Watermark into Digital Images,” 2018.
AnirbanPatra, ArijitSaha, Ajoy Kumar Chakraborty, Kallol Bhattacharya, “A New Approach to Invisible Water Marking of Color Images using Alpha Blending,” 2018.
Irshad Ahmad Ansari, Chang WookAhn and Millie Pant, “On the Security of “Block-based SVD image watermarking in spatial and transform domains”, 2018.
Alexander S. Komarov, “Adaptive Probability Thresholding in Automated Ice and Open Water Detection From RADARSAT-2 Images,” 2018.
Aoshuang Dong, RuiZeng, “Research and Implementation Based on Three-dimensional Model Watermarking Algorithm,” 2017.
EnjianBai, Yiyu Yang and Xueqin Jiang, “Image Digital Watermarking Based on a Novel Clock-controlled Generator,” 2017.
Oleg Evsutin, Roman Meshcheryakov, Viktor Genrikh, Denis Nekrasov and Nikolai Yugov, “An Improved Algorithm of Digital Watermarking Based on Wavelet Transform Using Learning Automata,” 2017.
Ritu Gill and Rishi Soni, “Digital Image Watermarking using 2-DCT and 2- DWT in Gray Images,” 2017.
Mohammad ShahabGoli and AlirezaNaghsh, “Introducing a New Method Robust Against Crop Attack In Digital Image Watermarking Using Two-Step Sudoku,” 2017.
Muhammad Usman, Irfan Ahmed, Shujaat khan, “SIT: A light weight encryption algorithm for secure internet of things,” international Journal of advanced computer science and applications, vol. 8, no.1, 2017.
Maria Almulhim, Noor Zaman, “Proposing secure and the lightweight authentication scheme for IOT based E health applications” International conference on advance communication technology; 2018.
Muhammad NaveedAman, KeeChaing Chua, “A light weight mutual authentication protocol for IOT system, 2017.
Krishnaveni, S. ., A. . Lakkireddy, S. . Vasavi, and A. . Gokhale. “Multi-Objective Virtual Machine Placement Using Order Exchange and Migration Ant Colony System Algorithm”. International Journal on Recent and Innovation Trends in Computing and Communication, vol. 10, no. 6, June 2022, pp. 01-09, doi:10.17762/ijritcc.v10i6.5618.
Mehdi Baahrami, Dong Li, MukeshSinghal, “Efficient parallel implementation of light weight data privacy method for cloud users; seventh international workshop on data intensive computing in clouds, 2016.
GauravBansod, AbhijitPatil, “An Ultra light weight design for security in pervasive computing” IEEE second international conference on big data security cloud, 2016.
ZahidMahmood, HuanshengNing, “Light weight two level session key management for end user authentication in internet of things” IEEE international conference on IOT, 2016.
Ayaz Hassan moon, UmmerIqbal, “Light weight authentication framework for WSN” International conference on Electrical, Electronics and Optimization techniques, 2016.
D Jamuna Rani, “Light weight cryptographic algorithm for medical internet of things”, Online international conference on Green Engineering and Technology, 2016.
SudhirSatpathy, Sanu Mathew, “Ultra low energy security circuits for IOT applications”, IEEE 34th international conference on computer design, 2016.
SainandanBayya Vankata, PrabhkarYellai, “ A new light weight transport method for secured transmission of data for IOT”, international journal of electrical, electronic engineering, 2016.
Amber Sultan, Xuelin Yang, “Physical layer data encryption using chaotic constellation rotation in OFDM-PON” Proceedings of 15th international Bhurban conference on applied science and technology Islamabad Pakistan, 2018.
Xuelin Yang, ZanweiShen, “Physical layer encryption algorithm for chaotic optical OFDM transmission against chosen plaintext attacks”, in ICTON 2016.
Han Chen, Xuelin Yang, “Physical layer OFDM data encryption using chaotic ZCMT precoding matrix”, IEEE, ICTON 2017.
Kabisha, M. S., Rahim, K. A., Khaliluzzaman, M., & Khan, S. I. (2022). Face and Hand Gesture Recognition Based Person Identification System using Convolutional Neural Network. International Journal of Intelligent Systems and Applications in Engineering, 10(1), 105–115. https://doi.org/10.18201/ijisae.2022.273
GaoBaojian, LuoYongling, HouAiqin, “New physical layer encryption algorithm based on DFT-S-OFDM system” International Conference on Mechatronic Sciences, Electric Engineering and Computer, Shenyang, China, 2013.
Meihua Bi, Xiaosong Fu, “A key space enhanced Chaotic encryption scheme for physical layer security in OFDM-PON”, IEEE photonics Journel”, 2017.
Dana Halabi, Salam Hamdan, “Enhance the security in smart home applications based on IOT-CoAP protocol.
Jongsoek Choi, Yongtae Shin, “study on information security sharing system among the industrial IOT service and product provider, IEEE ICOIN, 2018.
Jin HyeongJeon, Ki-Hyung Kim, “Block chain based data security enhanced IOT server platform, IEEE ICOIN, 2018.
MuhammetZekeriyaGunduz, Resul Das, “A comparision of cyber security oriented test beds for IOT based smart grids, IEEE 2016.
Himanshu Gupta, GarimaVarshney, “A security Framework for IOT devices against wireless threats, second international conference on telecommunication and networks, 2017.
Thomas Maurin, Lurent, George Caraiman, “IOT security assessment through the interfaces P-SCAN test bench platform, 2018.
Sanjay Kumar, AmbarDutta, “A Study on Robustness of Block Entropy Based Digital Image Watermarking Techniques with respect to Various Attacks,” 2016.
N. SenthilKumaran, and S. Abinaya, “Comparison Analysis of Digital Image Watermarking using DWT and LSB Technique,” 2016.
Harsha M. Patil and Prof .Baban U. Rindhe, “Study and Overview of Combined NSCT –DCT Digital Image Watermarking,” 2016.
Ravita, R., & Rathi, S. (2022). Inductive Learning Approach in Job Recommendation. International Journal of Intelligent Systems and Applications in Engineering, 10(2), 242–251. Retrieved from https://ijisae.org/index.php/IJISAE/article/view/1829
Alaria, S. K. "A.. Raj, V. Sharma, and V. Kumar.“Simulation and Analysis of Hand Gesture Recognition for Indian Sign Language Using CNN”." International Journal on Recent and Innovation Trends in Computing and Communication 10, no. 4 (2022): 10-14.
Dogiwal, Sanwta Ram, Y. S. Shishodia, Abhay Upadhyaya, Hanuman Ram, and Satish Kumar Alaria. "Image Preprocessing Methods in Image Recognition." International Journal of Computers and Distributed Systems 1, no. 3 (2012): 96-99.
Ashish Raj, Vijay Kumar, Satish Kumar Alaria, Vivek Sharma,. 2022. “Design Simulation and Assessment of Prediction of Mortality in Intensive Care Unit Using Intelligent Algorithms”. Mathematical Statistician and Engineering Applications 71 (2):355-67. https://doi.org/10.17762/msea.v71i2.97
Deepali Koul, Satish Kumar Alaria. 2018. “A New Palm Print Recognition Approach by Using PCA &Amp; Gabor Filter”. International Journal on Future Revolution in Computer Science &Amp; Communication Engineering 4 (4):38-45.
M. J. Traum, J. Fiorentine. (2021). Rapid Evaluation On-Line Assessment of Student Learning Gains for Just-In-Time Course Modification. Journal of Online Engineering Education, 12(1), 06–13. Retrieved from http://onlineengineeringeducation.com/index.php/joee/article/view/45
Rajput, B. S. ., Gangele, A. ., & Alaria, S. K. . (2022). Numerical Simulation and Assessment of Meta Heuristic Optimization Based Multi Objective Dynamic Job Shop Scheduling System. International Journal on Future Revolution in Computer Science &Amp; Communication Engineering, 8(3), 92–98.
Rajput, B. S. ., Gangele, A. ., Alaria, S. K. ., & Raj, A. . (2022). Design Simulation and Analysis of Deep Convolutional Neural Network Based Complex Image Classification System. International Journal on Future Revolution in Computer Science &Amp; Communication Engineering, 8(3), 86–91.
Alaria, S.K. and Kumar, Aashutosh, (2018). Implementation of new Cryptographic Encryption Approach for Trust as a Service (TAAS) in Cloud Environment. International Journal of Computer Application (2250-1797) Issue 8 Volume 4, July-August. Pp:18-35.